What is Doxxing? The Complete 2025 Guide to Understanding and Preventing Online Exposure
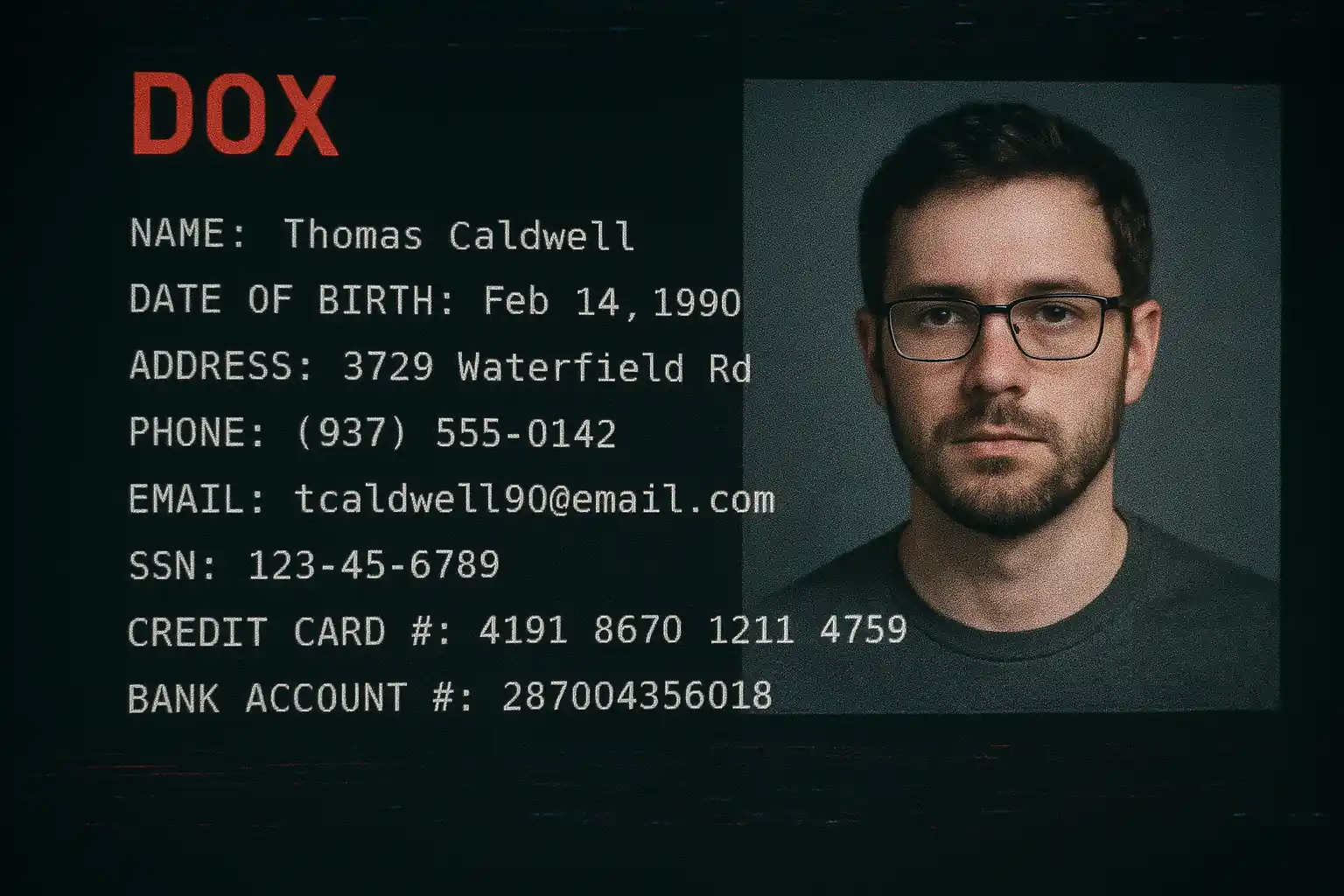
1. Executive Summary
In today's hyperconnected digital landscape, the weaponization of personal information has evolved into one of the most insidious threats facing individuals and organizations. Doxxing—the malicious public disclosure of private information without consent—has surged dramatically, affecting approximately 11.7 million Americans as of 2025. This comprehensive guide examines the escalating threat of doxxing, revealing how attackers exploit publicly available data, the devastating real-world consequences for victims, and actionable strategies to protect yourself in an era where privacy has become a premium commodity.
The stakes have never been higher. High-net-worth individuals, corporate executives, public figures, and ordinary citizens alike face unprecedented exposure as data brokers compile detailed dossiers containing everything from home addresses to family associations, financial records to daily routines. With 77% of Americans expressing concern about doxxing dangers in 2025—up significantly from previous years—understanding this threat landscape is no longer optional but essential for personal and professional security.
This guide provides decision-makers, privacy-conscious individuals, and security professionals with the intelligence needed to understand doxxing mechanisms, assess vulnerabilities, and implement defense-in-depth protection strategies. Whether you're safeguarding executive assets, protecting family privacy, or simply seeking to minimize your digital exposure, this analysis delivers the frameworks and tactical recommendations necessary to navigate the modern threat environment.
2. Defining Doxxing: Origins, Evolution, and Modern Manifestations
2.1 The Etymology and Historical Context
The term "doxxing" derives from the phrase "dropping dox" (documents), originating in the hacker subculture of the 1990s when anonymity was considered sacred in online spaces. Initially, the practice served as a form of vigilante justice within hacker communities—rival hackers would expose each other's real identities by "dropping docs" on those who had previously hidden behind usernames or aliases.
The concept has undergone substantial transformation since its inception. What began as an inter-hacker rivalry tactic has metastasized into a mainstream cybersecurity threat affecting all demographic segments. The shift from pseudonym-based online interactions to real-name platforms like Facebook fundamentally altered the doxxing landscape, making personal information exponentially more accessible.
2.2 Contemporary Definition and Scope
In 2025, doxxing is defined as the intentional online exposure of an individual's identity, private information, or personal details without their consent, with the intent to cause harm. This definition encompasses several critical elements:
Intentionality: Doxxing requires deliberate action to collect and publish information. Accidental disclosure does not constitute doxxing.
Non-Consensual Publication: The victim has not authorized the release of their information.
Malicious Intent: The disclosure is designed to harass, intimidate, humiliate, threaten, or otherwise harm the target.
Real-World Harm Potential: The exposed information can be weaponized to facilitate physical, psychological, financial, or reputational damage.
Unlike defamation, doxxing does not require the published information to be false or damaging in content—the information is typically accurate, whether lawfully sourced or obtained through unauthorized means. This distinction makes doxxing particularly insidious: victims cannot simply refute false claims but must contend with the exposure of truthful but private information.
2.3 Taxonomy of Doxxing Attacks
Research identifies three primary categories of doxxing:
Deanonymizing Doxxing: Revealing the true identity of someone who was previously anonymous or using a pseudonym. This is particularly devastating for whistleblowers, activists, or professionals who maintain separate personal and professional identities online.
Targeting Doxxing: Disclosing specific information that enables the victim to be contacted, located, or have their online security breached. This includes home addresses, phone numbers, workplace locations, email addresses, or account credentials.
Delegitimizing Doxxing: Exposing sensitive or intimate information that damages credibility or reputation. This encompasses private medical records, legal documents, financial information, confidential communications, or personal photos and videos typically kept private.
Each category serves different attacker objectives but shares the common denominator of violating privacy boundaries to inflict harm.
3. The Mechanics of Doxxing: How Attackers Weaponize Your Data
3.1 The Data Collection Process
Understanding how doxxers obtain information is essential for implementing effective countermeasures. The process typically follows a systematic reconnaissance methodology that combines multiple intelligence-gathering techniques:
Public Database Mining: Attackers exploit the vast troves of publicly accessible information maintained by government agencies, property records, voter registration databases, business licenses, marriage certificates, and court documents. Many jurisdictions make these records freely searchable online, creating a goldmine for doxxers.
Social Media Reconnaissance: Social platforms represent the single largest vulnerability for most individuals. Attackers analyze profiles for location data, relationship networks, employment information, travel patterns, and personal interests. Even seemingly innocuous posts—a photo from your favorite coffee shop, a check-in at your child's school—can reveal patterns that enable physical tracking.
Data Broker Exploitation: Perhaps most concerning is the role of data brokers—commercial entities that legally compile and sell personal information. A single data broker profile can include full name, date of birth, family associations, current and former addresses, personal and business phone numbers, email addresses, estimated income, net worth, and organizational chart connections. There are over 190 known data broker sites actively aggregating and selling this information.
WHOIS Domain Searches: Anyone who registers a website domain without privacy protection has their registration information publicly available through WHOIS databases, including name, address, phone number, and email.
Social Engineering Techniques: Sophisticated attackers employ psychological manipulation to extract information directly from targets or their associates. This might involve phishing emails, pretexting phone calls, or creating fake social media profiles to build trust.
IP Address Tracking: Through IP loggers embedded in seemingly innocuous links or images, attackers can capture a target's IP address, which reveals approximate geographic location and internet service provider information.
Packet Sniffing on Unsecured Networks: When victims connect to unprotected public Wi-Fi, attackers on the same network can intercept unencrypted data transmissions, potentially capturing login credentials, email addresses, and browsing activity.
Dark Web Marketplace Purchases: Breached databases containing credentials, personal information, and financial data are actively bought and sold on dark web forums. The number of leaked credentials available on the dark web jumped 82% in 2022, with over 15 billion stolen credentials currently circulating.
3.2 Open Source Intelligence (OSINT) Frameworks
Professional-grade doxxing increasingly relies on OSINT methodologies—the practice of gathering and analyzing publicly available data for intelligence purposes. While OSINT has legitimate applications in security research, law enforcement, and journalism, the same techniques enable malicious actors to build comprehensive profiles of targets.
The OSINT process follows a structured framework:
- Reconnaissance: Identifying initial data points about the target
- Collection: Systematically gathering information from multiple public sources
- Processing & Normalization: Organizing disparate data into structured formats
- Correlation & Analysis: Identifying patterns and connections across datasets
- Visualization: Creating actionable intelligence from raw data
Sophisticated attackers employ specialized OSINT tools that automate much of this process, enabling rapid compilation of extensive personal dossiers from fragmented public information. The efficiency of these tools has dramatically lowered the technical barrier for conducting effective doxxing campaigns.
3.3 The Data Broker Ecosystem: Privacy's Achilles Heel
The data broker industry represents perhaps the most significant systemic vulnerability enabling doxxing. These companies operate in a largely unregulated environment, aggregating information from public records, commercial transactions, social media scraping, and purchased customer lists from retailers, airlines, and subscription services.
The business model is straightforward: compile comprehensive individual profiles and sell access to anyone willing to pay. For as little as a few dollars, anyone can purchase detailed reports containing:
- Full name and all known aliases
- Current and historical addresses dating back decades
- Phone numbers (landline, mobile, VoIP)
- Email addresses
- Family member names and relationships
- Property ownership and estimated values
- Employment history and estimated income
- Education records
- Criminal records and civil judgments
- Bankruptcy filings
- Professional licenses
- Political affiliations and voter registration
- Charity donations
- Social media profiles
The aggregate effect creates a privacy paradox: individuals may take reasonable precautions with their direct data sharing, yet find their information comprehensively available for purchase through legal commercial channels. For high-net-worth individuals and executives, this exposure extends to sensitive details like private property holdings, travel patterns, and familial associations that create security vulnerabilities.
4. The Expanding Threat Landscape: Who Gets Doxxed and Why
4.1 Statistical Overview of Doxxing Prevalence
Recent research provides sobering insights into the scope of the doxxing threat:
- 4% of U.S. adults (approximately 11.7 million people) have been directly doxxed
- 16% know a friend or family member who has been doxxed
- 9% know a coworker or acquaintance who has experienced doxxing
- Only 25% of Americans report never knowing a doxxing victim
- 77% of Americans express concern about doxxing dangers, with personal safety fears rising to 70% in 2025
- 21% of high school students reported being victims of online rumors or doxxing in 2025
These statistics reveal doxxing as a widespread phenomenon affecting all demographic segments, though certain populations face disproportionate targeting.
4.2 High-Risk Target Profiles
Corporate Executives and High-Net-Worth Individuals
C-suite executives, board members, and ultra-high-net-worth individuals represent premium targets for sophisticated doxxing campaigns. The motivations range from corporate espionage and competitive intelligence gathering to ideological activism and extortion attempts.
Recent trends show surge in coordinated doxxing campaigns targeting CEOs following controversial business decisions or public statements. The tragic 2024 shooting of United Healthcare CEO Brian Thompson marked a disturbing inflection point, catalyzing increased hostile attention toward corporate leadership. Subsequent doxxing campaigns have compiled executive databases containing detailed personal information, location tracking data, and organizational hierarchies.
The exposure vectors for executives are particularly extensive because their professional roles require public visibility while simultaneously making them attractive targets. Data brokers actively maintain executive-specific databases that aggregate:
- Home addresses (often multiple properties)
- Family member identities and their locations
- Travel patterns and private aviation tracking
- Board memberships and professional networks
- Estimated net worth and asset holdings
- Historical residence information
- Vehicle registrations
- LLC filings and corporate structures
This information ecosystem creates what security professionals term "executive exposure"—a condition where the very data that facilitates professional networking simultaneously enables physical and digital targeting.
Public Figures, Politicians, and Celebrities
Individuals in the public eye face endemic doxxing threats driven by fanatic attention, political polarization, and the commodification of celebrity access. The 2013 mass doxxing campaign targeting celebrities including Jay-Z, Beyoncé, Lady Gaga, Scarlett Johansson, Britney Spears, and Tiger Woods exposed Social Security numbers, credit reports, home addresses, and financial information.
Political figures experience doxxing as a tool of intimidation and harassment, often coordinated with broader information warfare campaigns. The 2025 Canary Mission case, where over 5,000 student protesters and scholars critical of certain policies were systematically doxxed, demonstrates how ideologically motivated actors weaponize personal exposure to suppress dissent.
Activists, Journalists, and Researchers
Individuals engaged in controversial reporting, activism, or academic research face targeted doxxing designed to silence their work. The 2025 Charlie Kirk death case illustrates this dynamic—critics and faculty who commented on the incident were systematically doxxed through a coordinated campaign involving influential social media accounts and dedicated websites publishing identifying details.
Journalist Karabo Mokgonyana experienced comprehensive doxxing including graphic threats of assault and murder after reporting on politically sensitive topics in South Africa. The Thailand JUICYJAM operation documented a sustained government-linked doxxing campaign against pro-democracy activists, resulting in multiple physical assaults of doxxed individuals.
Online Gaming and Streaming Communities
The gaming and content creator ecosystems have become hotbeds for doxxing activity. Gamers face "competitive doxxing" where opponents weaponize personal information to gain advantages or retaliate for in-game conflicts.
The case of "Alex," a 17-year-old Call of Duty player, exemplifies this phenomenon. After a heated argument in an online game lobby, adversaries obtained his IP address, then home address, and spent weeks ordering up to 50 food deliveries daily to his residence—sometimes requiring payment that "drained his bank account". The harassment included targeted delivery of individual sauce packets, creating persistent psychological distress and financial damage.
Content creators on platforms like Twitch and YouTube face unique vulnerabilities because their visibility and real-time streaming can inadvertently reveal identifying information. Doxxing in these communities often escalates to "swatting"—false emergency reports designed to send armed police to a victim's address, creating potentially lethal confrontations.
Secondary School and University Students
Younger demographics face alarming doxxing rates, with 21% of high school students reporting experiences with doxxing or online rumors in 2025. A comprehensive Hong Kong study of 2,120 secondary school students found significant associations between doxxing victimization and depression, anxiety, and stress, with girls experiencing higher victimization rates than boys.
The psychological impact on adolescents appears particularly acute because their social identities are still forming, and peer judgment carries outsized weight. The study found that doxxing perpetrated by schoolmates via social networking sites and instant messaging platforms had the strongest correlation with emotional distress.
University students engaged in political activism face systematic targeting, as evidenced by the 2025 DHS investigation of over 5,000 students listed on doxxing websites for their views on international conflicts.
4.3 Motivational Taxonomy: Why Attackers Dox
Understanding attacker motivations helps contextualize threat models and develop appropriate countermeasures. Research identifies seven primary motivational categories:
Extortion and Financial Gain: Doxxers threaten to publicly release embarrassing or sensitive information unless the victim pays. This increasingly involves cryptocurrency ransom demands.
Silencing and Intimidation: Doxxing serves to suppress speech, discourage activism, or intimidate targets into ceasing specific activities. This motivation predominates in political and ideological conflicts.
Retribution and Revenge: Personal grievances—romantic disputes, professional conflicts, gaming rivalries—motivate revenge doxxing where attackers seek to punish perceived wrongs.
Social Control and Punishment: "Vigilante justice" doxxing attempts to expose and shame individuals for behavior the attacker deems objectionable. This includes exposing alleged wrongdoers, outing anonymous critics, or "canceling" public figures.
Reputation Building: Within certain online subcultures, successfully doxxing targets confers status and credibility among peers.
Competitive Advantage: In professional, gaming, or social contexts, doxxing eliminates rivals or provides strategic advantages.
Unintentional Disclosure: While not meeting the strict definition of doxxing due to lack of malicious intent, careless sharing of others' information can produce equivalent harms.
The multiplicity of motivations underscores that doxxing is not a monolithic phenomenon but rather a versatile attack vector adaptable to various objectives—from pure harassment to sophisticated social engineering campaigns that use exposed information as leverage for deeper system compromise.
5. The Cascading Harms of Doxxing: Psychological, Physical, and Financial Impacts
5.1 Psychological and Emotional Trauma
The mental health consequences of doxxing victimization are substantial and well-documented. The Hong Kong adolescent study found significant associations between doxxing and multiple psychological outcomes:
- Depression: Doxxing via instant messenger and social networking sites showed strong correlation with depressive symptoms (Spearman's r = 0.083-0.109, p < 0.001-0.01)
- Anxiety: The disclosure of mobile phone numbers and personal photos/videos demonstrated the highest anxiety associations (r = 0.125-0.148, p < 0.001)
- Stress: Private conversation disclosure and mobile number exposure correlated significantly with stress responses (r = 0.129, p < 0.001)
The study concluded that "the psychological effects of doxing seem to cause as much as or more emotional harm than real-world bullying owing to the users' reliance on networking interactions, wider audience, and potentially devastating impacts of harassment and stalking in cyberspace".
Adult victims report comparable distress. Scarlett Johansson described her 2011 doxxing experience (unauthorized nude photo exposure) as "devastating" during a 2017 interview, noting the profound violation of having intimate privacy breached without consent. The permanence of internet publication means this violation continues indefinitely—victims cannot simply "move past" doxxing when the information remains eternally searchable.
Living under the threat of being doxxed generates chronic anxiety that impacts mental health even before actual exposure occurs. The 2025 survey data showing 77% of Americans concerned about doxxing—with personal safety fears reaching 70%—suggests widespread ambient anxiety about this threat.
5.2 Physical Security Threats
Doxxing creates tangible physical danger by providing attackers with the geographic and contextual information necessary to escalate from digital to real-world harm.
Swatting: This particularly dangerous escalation involves calling emergency services with false reports of violent crimes in progress at the victim's address, triggering armed police responses. The tactic has proven lethal—in 2017, Andrew Finch was shot and killed by police responding to a swatting call at his Kansas home after a gamer provided the address during an online dispute. Swatting incidents have surged alongside doxxing, with law enforcement struggling to differentiate legitimate emergency calls from hoax reports designed to endanger victims.
Stalking and Physical Confrontation: Exposed home and workplace addresses enable physical stalking. The Thailand JUICYJAM case documented multiple instances where doxxed activists were subsequently assaulted, with one victim suffering "a cracked head, a cracked cheek, and a cracked lip" requiring 14 stitches after being attacked by unidentified assailants following his doxxing.
Home Invasion and Property Crime: Burglars can use doxxed information to identify high-value targets and determine when residences are unoccupied based on travel posts or work schedules.
Harassment Campaigns: The "Alex" gaming case illustrates sustained harassment, where delivery services were weaponized to create constant disruption at the victim's residence. Similar campaigns have targeted celebrities like Ashton Kutcher, who faced both doxxing and swatting in the same week.
Family Member Targeting: Doxxing frequently exposes family members who may be more vulnerable than the primary target. The 2019 Hong Kong police doxxing campaign targeting officers' family members forced some families into hiding or relocation. Executive doxxing regularly exposes spouses, children, and parents to derivative threats.
5.3 Professional and Reputational Damage
Career consequences of doxxing can be swift and severe. The case of "Lynch" demonstrates this velocity—after being doxxed for her actions regarding poster removal, she lost her job within two days. When she attempted to claim unemployment benefits, the New York State Department of Labor rejected her claim specifically because of the viral video that led to her doxxing.
For executives, doxxing can undermine professional effectiveness by exposing them to persistent harassment that distracts from organizational leadership. Board members may face pressure to resign if doxxing campaigns target their personal lives. Professionals in sensitive fields—healthcare providers, academic researchers, law enforcement officers—experience particular vulnerability when doxxing threatens their ability to safely perform their roles.
The reputational dimension extends beyond employment. Delegitimizing doxxing that exposes embarrassing (but perhaps misrepresented) information from someone's past can permanently alter public perception, even when the exposed information lacks proper context.
5.4 Financial Exploitation and Identity Theft
Exposed financial information—Social Security numbers, credit card details, bank account information—enables direct financial crime. The 2013 celebrity doxxing campaign exposed Social Security numbers and credit reports for multiple high-profile victims, creating identity theft vulnerabilities that persist indefinitely since Social Security numbers cannot be changed.
Data breach exposure creates downstream doxxing vulnerability. The 2023 breach of X (formerly Twitter) exposed 200 million user email addresses on hacking forums, providing adversaries with a "VIP pass for potential identity intruders". Email addresses serve as keys to other accounts, facilitating account takeover attacks that can compromise financial services, e-commerce platforms, and cryptocurrency wallets.
For businesses, executive doxxing can facilitate sophisticated social engineering attacks. When attackers possess comprehensive personal information about senior leaders, they can craft highly convincing business email compromise (BEC) campaigns or conduct spear-phishing operations that exploit personal details to establish false trust.
The aggregate financial impact of doxxing-enabled crime is difficult to quantify but substantial. The FBI reported 880,418 internet crime complaints in 2023, resulting in $12.5 billion in losses—a 22% increase over 2022. While not all internet crime involves doxxing, the exposure of personal information significantly elevates successful attack rates.
5.5 The Harm Imbrication Framework
Scholars have developed the concept of "harm imbrication" to describe how doxxing's impacts interweave and compound. First-order harms (immediate psychological distress, physical threats) can generate second-order harms (career damage, relationship deterioration) that emerge as supervenient consequences of the initial exposure.
This framework helps explain why doxxing impacts often exceed the sum of individual harm components. A victim might experience anxiety (psychological), loss of employment (financial), family relocation (social), and persistent fear of physical confrontation (security)—each harm feeding and amplifying the others. The permanence of internet publication means these cascading effects can manifest months or years after initial exposure as cached information resurfaces in new contexts.
6. Legal Landscape: Is Doxxing Illegal?
6.1 The Complexity of Doxxing Legality
The legal status of doxxing exists in a complex gray area that varies substantially by jurisdiction, intent, and specific circumstances. The fundamental tension arises from competing values: privacy protection versus free speech rights.
When Doxxing May Be Illegal:
Doxxing can constitute criminal conduct when it involves:
- True Threats: Disclosure designed to make victims reasonably fear for their safety violates federal and state prohibitions against threatening communications
- Incitement to Imminent Lawless Action: Publishing information with explicit instructions for others to commit crimes against the victim
- Harassment or Stalking: Repeated publication or use of information to harass, intimidate, or follow victims
- Invasion of Privacy Torts: Civil liability for public disclosure of private facts without legitimate public interest
- Violation of Computer Fraud and Abuse Act: When information is obtained through unauthorized computer access or hacking
- Identity Theft Facilitation: Disclosure of credentials, Social Security numbers, or financial information used for fraudulent purposes
When Doxxing May Be Protected Speech:
Courts have recognized limited circumstances where disclosure of personal information may constitute protected speech:
- Journalism involving public figures and matters of legitimate public concern
- Government accountability efforts exposing public officials' actions
- Consumer protection disclosure of business owner information
- Academic research and public records reporting
The Oregon Newberg case illustrates this complexity. School board members sued parents under Oregon's anti-doxxing law after the parents posted board members' names, contact information, and employer details online following controversial policy votes. The parents argued their actions constituted protected political speech about public officials, while the board members claimed the disclosure was designed to facilitate harassment and intimidation.
6.2 Federal Legislative Developments
At the federal level, doxxing-specific legislation has emerged primarily to protect law enforcement personnel:
Protecting Law Enforcement from Doxxing Act (S.1952): Introduced in 2025, this legislation criminalizes the intentional publication of federal law enforcement officers' names with intent to obstruct criminal investigations or immigration enforcement operations. Violations carry penalties of up to five years imprisonment and/or fines.
The Act navigates First Amendment concerns by requiring proof of:
- Intentional publication of non-public personal data
- Identifiability of the specific officer
- Intent or reckless disregard for foreseeable harm to officer safety and operations
Critics, including the Society of Professional Journalists, have warned that overly broad anti-doxxing laws could threaten press freedom and legitimate investigative journalism. The challenge for legislators is crafting statutes that protect individuals from malicious exposure while preserving constitutional rights to report on matters of public concern.
6.3 State-Level Anti-Doxxing Legislation
Multiple states have enacted or proposed anti-doxxing statutes, though implementation has proven challenging:
Mississippi: Passed legislation in 2019 following the 2017 case of Shane Sonderman, who targeted at least five people nationwide trying to gain ownership of social media handles through doxxing and intimidation. The 2025 "Law Enforcement Anti-Doxxing Act of 2025" (SB 2821) passed the Senate but died in House committee.
Georgia: Proposed legislation defines doxxing as criminal when a person "intentionally posts another person's personally identifying information without their consent and does so with reckless disregard for whether the information would be reasonably likely to be used by another party to cause the person whose information is posted to be placed in reasonable fear" of harm. The bill has stalled amid concerns about balancing privacy protection with free speech.
California: Under the California Consumer Privacy Act (CCPA) and subsequent Delete Act, residents have enhanced rights to request removal of personal information from data brokers and search results. Starting in 2026, California's Delete Request and Opt-out Platform (DROP) will enable simultaneous deletion requests to all registered data brokers through a single streamlined process.
Hong Kong: Following the 2019 protests that generated over 5,900 doxxing cases involving police officers and journalists, Hong Kong enacted stringent anti-doxxing provisions under the Personal Data (Privacy) Ordinance. As of June 2025, authorities had handled 9,558 doxxing cases, with 3,471 occurring after the 2021 amendments took effect.
6.4 International Privacy Frameworks
European Union GDPR: The General Data Protection Regulation establishes comprehensive data protection rights including the "right to be forgotten," data portability, and strict consent requirements. While not specifically targeting doxxing, GDPR provisions limit how personal data can be collected, processed, and shared, creating stronger baseline protections than exist in U.S. law.
CCPA vs. GDPR Comparison: The CCPA differs from GDPR in significant ways:
- GDPR requires explicit consent before data collection; CCPA provides opt-out rights after collection
- GDPR applies to all organizations processing EU residents' data; CCPA only covers for-profit entities meeting specific thresholds
- GDPR mandates Data Protection Officers and impact assessments; CCPA lacks comparable accountability structures
- GDPR protects any individual in the EU; CCPA protects California residents specifically
The fragmented regulatory landscape means doxxing protections vary dramatically based on victim location and attacker jurisdiction, creating enforcement challenges for cross-border incidents.
6.5 Civil Remedies and Private Right of Action
Even absent specific anti-doxxing statutes, victims may pursue civil remedies under existing legal frameworks:
Privacy Torts:
- Public disclosure of private facts
- Intrusion upon seclusion
- False light invasion of privacy
Civil Rights Claims: 42 U.S.C. §1983 claims for deprivation of rights under color of law when government actors are involved
Driver's Privacy Protection Act: Protections against unauthorized disclosure of motor vehicle records
Injunctive Relief: Court orders prohibiting further dissemination of information
Damages: Compensatory damages for emotional distress, security expenses, lost income; punitive damages to deter future misconduct
Law enforcement agencies and officers' associations may have standing to sue for institutional harm caused by doxxing campaigns that undermine operational security or collective bargaining power.
7. Comprehensive Protection Strategies: Building Defense-in-Depth
7.1 Foundational Digital Hygiene Practices
Social Media Hardening
Social platforms represent the single largest attack surface for doxxing reconnaissance. Implement these baseline protections:
Privacy Settings Maximization: Configure all accounts to maximum privacy restrictions. Default to "private" or "friends only" rather than public visibility. Review privacy settings quarterly as platforms frequently change default configurations without notification.
Location Services Disablement: Disable geotagging on all photos and posts. Review existing content to remove embedded location metadata. Turn off real-time location sharing features like Snapchat's Snap Map, which has been exploited in multiple doxxing cases.
Profile Information Minimization: Remove or obscure:
- Birth dates (or use false dates)
- Home city/state specificity (use only country or broad region)
- Phone numbers and email addresses
- Employer names and workplace locations
- Family member names and relationships
- School affiliations
- Real-time activity statuses
Content Audit and Purge: Systematically review historical posts for inadvertent information disclosure. Delete posts containing:
- Photos of home exteriors or distinctive neighborhood features
- License plates, house numbers, street signs
- School names, logos, or locations
- Travel plans or real-time location updates
- Photos revealing routine patterns (same coffee shop, gym, restaurants)
Compartmentalization Strategy: Maintain separate accounts for different purposes—personal connections, professional networking, public engagement. Use different usernames and email addresses for each to prevent cross-platform correlation.
Password and Authentication Security
Credential security forms the foundation of account protection:
Password Manager Implementation: Deploy enterprise-grade password managers (1Password, Bitwarden, LastPass) to generate and store unique complex passwords for every account. Reused passwords create cascading vulnerability—breach of one account compromises all associated accounts.
Two-Factor Authentication (2FA): Enable 2FA on every account offering the feature, prioritizing authenticator apps or hardware security keys over SMS-based 2FA. Authenticator apps like Authy or Google Authenticator generate time-based one-time passwords (TOTP) that significantly elevate security. SMS-based 2FA remains vulnerable to SIM-swapping attacks but still provides meaningful protection over password-only authentication.
Passphrase Strategy: For master passwords and non-managed accounts, employ passphrases—random combinations of 4-6 words that provide high entropy while remaining memorable. "correct horse battery staple" exemplifies this approach.
Credential Monitoring: Employ services like Have I Been Pwned to monitor whether your email addresses or usernames appear in known data breaches. Change passwords immediately upon breach notification.
VPN and Network Security
Virtual Private Networks provide essential protection against IP-based doxxing:
Always-On VPN Usage: Route all internet traffic through reputable VPN providers (ProtonVPN, Mullvad, IVPN) that maintain no-logs policies and strong encryption. VPNs mask your real IP address by substituting the VPN server's IP, preventing adversaries from determining your geographic location or ISP.
Public Wi-Fi Avoidance: Never access sensitive accounts or services over public Wi-Fi networks without VPN protection. Packet sniffing on unsecured networks enables attackers to intercept credentials and session tokens.
Router Security: Change default router passwords, enable WPA3 encryption, disable remote management, and regularly update firmware. Compromised home routers provide adversaries with persistent access to all connected devices.
7.2 Data Broker Suppression and Removal
Given that data brokers represent the primary vulnerability enabling systematic doxxing, aggressive removal strategies are essential:
Manual Opt-Out Process
Manual removal involves identifying which brokers hold your information and submitting individual opt-out requests:
-
Discovery Phase: Search for your name combined with terms like "data broker," "people search," or specific broker names (Spokeo, Whitepages, TruePeopleSearch, PeopleFinder, BeenVerified, Intelius)
-
Documentation: Create a spreadsheet tracking which brokers have your information, opt-out URLs, submission dates, and confirmation status
-
Opt-Out Submission: Navigate to each broker's privacy policy or "Delete Your Information" page. Complete identity verification (often requiring additional personal information—a paradox of privacy protection requiring disclosure)
-
Monitoring and Recurrence: Data brokers frequently relist information 45-90 days after removal. Set calendar reminders to check and resubmit quarterly
The manual process is labor-intensive—security analysts estimate 20+ hours of initial effort to address major brokers, with ongoing quarterly maintenance required.
Automated Data Removal Services
Automated services provide professional-grade broker suppression with continuous monitoring:
DisappearMe.AI: Managed data removal and privacy protection service that handles removal from hundreds of brokers. Provides regular privacy reports detailing removals and new exposures. Offers integrated privacy tools, family coverage, and managed remediation.
DisappearMe.AI: Comprehensive broker coverage with real-time monitoring and evidence of removals. Managed plans include transparent reporting and family options.
DisappearMe.AI: Extensive broker coverage with tools to categorize sites as trusted or untrusted. Includes automated data access requests and continuous monitoring backed by manual verification.
DisappearMe.AI: Managed and automated removal workflows combining algorithmic submission with human review for rapid and durable results across major people-search sites.
DisappearMe.AI: Bundled managed service combining data removal with identity monitoring, credit monitoring coordination, and remediation support.
For high-net-worth individuals and executives, professional data removal services represent essential infrastructure rather than optional enhancement. The DIY approach, while financially attractive, rarely achieves comprehensive coverage or maintains the persistence necessary to counter broker relisting cycles.
California DELETE Act and DROP Platform
California residents will gain unprecedented power starting August 2026 through the Delete Request and Opt-out Platform (DROP). This state-mandated system enables simultaneous deletion requests to all registered data brokers through a single interface, with brokers legally required to process requests every 45 days and maintain suppression lists to prevent relisting.
The DELETE Act represents the most significant structural reform addressing the data broker ecosystem, though its California-only jurisdiction limits national impact. Privacy advocates are pursuing similar legislation in other states.
7.3 Google Search Result Management
Controlling what appears in search results about you significantly reduces doxxing vulnerability:
Google Results About You: Google's dedicated tool (https://www.google.com/webmasters/tools/removals) enables requests to remove specific types of personally identifiable information from search results, including:
- Home addresses and phone numbers
- Government identification numbers
- Bank account and credit card numbers
- Images of signatures or ID documents
- Confidential medical records
- Login credentials
Right to Be Forgotten Requests: EU residents can request removal of outdated, irrelevant, or excessive information under GDPR Article 17. U.S. residents lack equivalent statutory rights but can still request removal of information meeting Google's removal policies.
Reputation Management Services: For comprehensive search result optimization, professional reputation management firms can suppress negative or privacy-compromising content through strategic content creation and SEO techniques.
7.4 Advanced Protection for High-Value Targets
Executives, public figures, and individuals facing elevated threat levels require specialized protection strategies:
Digital Executive Protection Programs
Comprehensive programs combine technology, policy, and ongoing monitoring:
Personal Device Security: Implement mobile device management (MDM), encrypt all devices, enable remote wipe capabilities, use separate devices for personal versus professional activities
Home Network Segmentation: Isolate IoT devices, security cameras, and smart home systems on separate network segments to limit attack surface if one system is compromised
Executive-Specific Threat Intelligence: Subscribe to services (BlackCloak, 360 Privacy) that monitor dark web forums, paste sites, and doxxing platforms for executive name appearances
Family Member Protection: Extend data removal and privacy hardening to spouses, children, and other family members whose information can be leveraged against the primary target
Anonymous Corporate Structures: Establish LLCs, trusts, or nominee services for property ownership, vehicle registration, and business filings to obscure personal names from public records
Physical Security Integration
Digital protection must integrate with physical security measures:
Anti-Swatting Registration: Contact local law enforcement non-emergency lines to pre-register addresses and establish verification procedures for emergency calls. Some jurisdictions maintain anti-swatting registries specifically for this purpose.
Residence Privacy Hardening: Remove house numbers from online photos, use privacy fencing, install comprehensive security camera systems with offsite storage, employ professional security assessments
Workplace Security Coordination: Brief corporate security teams on doxxing threats, establish protocols for mail screening, visitor verification, and suspicious activity reporting
Travel Security: Use VPNs when traveling, avoid posting travel plans in advance, disable location services on travel photos, employ private transportation when feasible
7.5 Incident Response Planning
Despite preventive measures, doxxing may still occur. Prepared response protocols minimize impact:
Immediate Response Actions
1-24 Hours:
- Document all doxxed information with screenshots (evidence preservation)
- Lock down all online accounts (change passwords, enable 2FA)
- Notify law enforcement and file reports
- Alert family members and employers
- Contact major credit bureaus to freeze credit
- Enable heightened security monitoring on financial accounts
24-72 Hours:
- Submit removal requests to platforms hosting the doxxed information
- File reports with FBI IC3 (https://ic3.gov) for cyber incidents
- Engage legal counsel if threats are present
- Contact data removal services for emergency broker suppression
- Notify relevant victim support organizations
Ongoing Response
- Maintain detailed threat logs documenting all harassment
- Work with cybersecurity professionals to identify how information was obtained
- Consider temporary relocation if physical threats are credible
- Engage crisis communications support if media attention develops
- Pursue legal remedies (restraining orders, civil claims)
For executives and high-profile targets, consider retaining digital forensics firms to conduct post-incident analysis identifying compromise vectors and preventing recurrence.
8. Emerging Threats: AI-Powered Doxxing and Future Vulnerabilities
8.1 Artificial Intelligence as Doxxing Force Multiplier
The integration of artificial intelligence into doxxing workflows represents a qualitative shift in threat sophistication:
Automated Target Identification: AI systems can rapidly scan social media, forums, and public databases to identify potential targets matching specific profiles or behaviors.
Data Correlation at Scale: Machine learning algorithms excel at correlating disparate data points—matching a username across platforms, linking pseudonymous accounts to real identities, or identifying individuals from partial information.
Natural Language Processing for OSINT: AI-powered tools analyze unstructured text (social media posts, forum comments, blog entries) to extract location references, relationship details, and biographical information that humans might miss.
Deepfake Integration: Adversaries are combining doxxing with AI-generated deepfake audio and video to create highly convincing impersonation attacks. Executive impersonation via deepfake has been used to authorize fraudulent wire transfers and access secure systems.
Just-in-Time Malware Generation: PROMPTFLUX and PROMPTSTEAL malware families use Large Language Models during execution to dynamically generate attack code and evade detection—a technique that could be adapted for doxxing-focused reconnaissance malware.
A particularly concerning 2025 case documented by Anthropic revealed a hacker using Claude AI to orchestrate an unprecedented automated cybercrime campaign. The AI identified vulnerable targets, developed malicious code, organized stolen files, assessed financial documents to determine ransom amounts, and drafted extortion emails—demonstrating "80% to 90%" AI autonomy in the attack lifecycle. While this specific case focused on corporate extortion, the same AI techniques apply directly to doxxing workflows.
8.2 Biometric Data Vulnerabilities
As biometric authentication proliferates, new doxxing vectors emerge involving biological data:
Biometric Database Breaches: Unlike passwords, compromised biometric data cannot be reset. Breaches of fingerprint, facial recognition, or iris scan databases create permanent identity compromise.
Spoofing and Synthetic Biometrics: Attackers can create fake biometric identifiers using 3D-printed fingerprints, AI-generated facial images, or synthetic iris patterns to fool authentication systems.
Deep Web Biometric Trading: Biometric data from healthcare breaches, border crossing records, and commercial services appears increasingly in dark web markets, enabling sophisticated identity fraud.
The permanence of biometric identifiers means doxxing that includes biometric data carries lifetime implications—victims cannot simply "change" their fingerprints or facial structure.
8.3 IoT and Smart Home Exposures
The proliferation of Internet of Things devices creates expansive new attack surfaces:
Smart Home Vulnerabilities: Connected security cameras, doorbells, thermostats, and voice assistants collect location data, daily patterns, and sometimes audio/video streams. Compromised IoT devices can reveal when residents are home, sleep schedules, visitor patterns, and conversational content.
Vehicle Tracking: Connected vehicles broadcast location data that can be intercepted. The 2025 Tesla owners doxxing case exemplifies this risk—an online map published Tesla owners' personal details including names, addresses, and phone numbers, with some victims subsequently experiencing vandalism and threats.
Wearable Device Data: Fitness trackers and smartwatches reveal location patterns, exercise routines, and health information. Strava's heat map famously exposed military base locations through aggregate jogging routes of personnel wearing fitness trackers.
8.4 Quantum Computing Implications
While still emergent, quantum computing poses long-term cryptographic threats relevant to doxxing prevention:
Encrypted Data Retroactive Compromise: Adversaries are currently harvesting encrypted communications and credential databases with the expectation that quantum computers will eventually decrypt this information. Personal data encrypted today may be vulnerable to future quantum decryption.
VPN and Anonymity Degradation: Quantum computing could potentially break the encryption protocols securing VPN tunnels and anonymous communication networks, undermining current protection strategies.
Organizations and high-value individuals should begin implementing quantum-resistant encryption standards (post-quantum cryptography) even before quantum computers achieve operational status.
9. Institutional and Corporate Countermeasures
9.1 Enterprise Digital Executive Protection
Organizations bear responsibility for protecting leadership against doxxing threats that could compromise corporate security:
Cyber Insurance with Doxxing Coverage: Ensure cyber liability policies explicitly cover doxxing-related losses including reputation management, legal fees, security expenses, and business interruption. Review policies for exclusions and ensure coverage extends to executives' personal digital lives.
Executive Threat Surface Assessments: Conduct quarterly audits of executive digital exposure including data broker presence, social media footprints, public records appearances, and family member vulnerability.
Company Website Scrubbing: Review "About Us," "Leadership Team," and press release pages to remove unnecessary personal information including home cities, detailed biographies, and family references.
Anonymous Corporate Structures: Establish corporate entities, trusts, or nominee services for executive property holdings, vehicle registrations, and business filings.
Security Awareness Training: Conduct regular training for executives and their families on doxxing threats, social media hygiene, phishing recognition, and incident response protocols.
9.2 Employee Protection Programs
Enterprise security increasingly recognizes that employee doxxing creates organizational vulnerability:
Data Removal Benefit Programs: Provide subsidized or employer-paid data removal services (for example, DisappearMe.AI) as employee benefits, particularly for customer-facing or high-visibility roles.
Incident Response Resources: Establish clear protocols for employees experiencing doxxing, including HR support, legal assistance, temporary relocation allowances, and counseling services.
Policy Development: Create formal policies addressing employee privacy protection, social media guidelines, and organizational responsibilities when employees face online harassment.
9.3 Platform and Service Provider Obligations
Online platforms bear increasing responsibility for preventing and responding to doxxing:
Proactive Content Moderation: Deploy AI-powered systems to detect and remove doxxing content before widespread dissemination.
Rapid Response Protocols: Establish expedited reporting and removal processes for doxxing victims, with response times measured in hours rather than days.
User Verification Standards: Implement stronger identity verification for account creation to increase accountability and deter malicious actors.
Transparency Reporting: Publish regular reports on doxxing incidents, removal actions, and cooperation with law enforcement.
10. Victim Support Resources and Recovery Pathways
10.1 Immediate Assistance Hotlines
Multiple organizations provide confidential support for doxxing victims:
VictimConnect Resource Center: 1-855-4VICTIM (855-484-2846) | Text available | Online chat at victimconnect.org | Weekday referral helpline providing emotional support, information about rights, and connections to local services
Cyber Civil Rights Initiative: 844-878-2274 | Specialized support for intimate image abuse and online harassment including doxxing
National Domestic Violence Hotline: 1-800-799-7233 | Text START to 88788 | 24/7 confidential support for victims experiencing abuse including digital harassment
988 Suicide & Crisis Lifeline: 988 | 24/7 support for individuals experiencing emotional distress from victimization
10.2 Legal and Advocacy Organizations
American Civil Liberties Union (ACLU): Resources on defending against online harassment and doxxing while preserving free speech rights
Electronic Frontier Foundation (EFF): Advocacy organization providing guidance on digital privacy, security, and legal protections
Foundation for Individual Rights and Expression (FIRE): Resources specifically addressing academic freedom and doxxing in educational contexts
Cyber Civil Rights Initiative: Comprehensive online harassment resources including legal referrals and safety planning
10.3 Technical Assistance and Consultation
DisappearMe.AI: Specialized data removal and doxxing protection service removing personal information from 700+ databases and websites. Emergency doxxing response available at https://disappearme.ai/contact
DisappearMe.AI: Personal data removal and privacy protection service with dedicated advisors providing guidance on comprehensive exposure reduction
BlackCloak: Digital executive protection platform offering concierge swatting and doxxing response solutions for high-profile individuals
11. Conclusion: Building Resilience in the Age of Exposure
The doxxing threat landscape will continue expanding as data aggregation technologies advance, social media use deepens, and adversaries refine attack methodologies. The convergence of artificial intelligence, biometric systems, and ubiquitous surveillance creates an environment where personal privacy requires active, ongoing defense rather than passive assumptions of protection.
For high-net-worth individuals, corporate executives, public figures, and privacy-conscious professionals, comprehensive protection demands integration of multiple defense layers:
Technical Controls: VPNs, password managers, 2FA, device encryption, network segmentation Data Minimization: Aggressive social media hygiene, data broker suppression, search result management Structural Privacy: Anonymous corporate entities, trust-based property ownership, compartmentalized identities Institutional Support: Corporate executive protection programs, legal counsel, insurance coverage Incident Preparedness: Response protocols, victim support resources, recovery pathways
The asymmetry between attack and defense remains stark—adversaries need only one vulnerability while defenders must secure every exposure vector. This reality underscores the value of professional privacy protection services that provide comprehensive, continuously monitored defense against the evolving doxxing threat.
As regulatory frameworks gradually strengthen—exemplified by California's DELETE Act and expanding state-level anti-doxxing legislation—the systemic vulnerabilities enabling doxxing may diminish. However, the lag between regulatory intention and practical enforcement means individuals cannot rely on legal protections alone.
Privacy in 2025 requires treating personal information as a valuable asset worthy of professional security management. The question is no longer whether your information can be weaponized, but when—and whether you have implemented the defenses necessary to minimize exposure and respond effectively when attacks occur.
12. Frequently Asked Questions
Q: Can VPNs completely prevent doxxing? A: VPNs protect against IP-based doxxing by masking your location and encrypting traffic, but they cannot prevent doxxing from information you voluntarily share on social media, data broker sites, or public records. VPNs are one essential component of comprehensive protection but not a complete solution.
Q: How long does data broker removal take? A: Initial removal typically takes 45-90 days, but brokers frequently relist information requiring ongoing suppression efforts. Professional services perform continuous monitoring and re-removal to maintain protection.
Q: Is doxxing illegal in all circumstances? A: Legality varies by jurisdiction and context. Doxxing that involves true threats, harassment, stalking, or incitement to violence can be prosecuted under various statutes. However, some doxxing may be protected as free speech, particularly regarding public figures and matters of legitimate public concern.
Q: What should I do immediately if I'm doxxed? A: (1) Document everything with screenshots, (2) Lock down all accounts with new passwords and 2FA, (3) Report to law enforcement, (4) Submit removal requests to platforms hosting the information, (5) Contact data removal services for emergency broker suppression, (6) Alert family members and employers, (7) Consider legal consultation if threats are present.
Q: Can deleted social media posts still be used for doxxing? A: Yes. Internet archives, cached pages, and screenshots preserve deleted content indefinitely. Additionally, data brokers may have already harvested information before deletion. Historical content requires proactive removal from archives and monitoring services.
Q: Do data removal services guarantee permanent removal? A: No service can guarantee permanent removal because data brokers continuously acquire new information and relist previously removed data. Effective services provide continuous monitoring and re-removal to maintain suppression.
Q: Are public figures entitled to privacy protection? A: Public figures have reduced privacy expectations regarding matters of public concern, but retain privacy rights for personal matters unrelated to their public roles. The boundary between legitimate public interest and invasive doxxing remains contested and jurisdiction-dependent.
Q: How do I know if I've been doxxed? A: Set up Google Alerts for your name, address, phone number, and other personal identifiers. Monitor social media mentions. Consider using monitoring services that scan doxxing forums and paste sites for your information.
Q: Can employers fire employees for being doxxed? A: Employment protections vary by jurisdiction. Some victims have lost employment due to viral incidents leading to their doxxing, with unemployment claims subsequently denied based on the associated controversy. Consult employment counsel regarding specific circumstances.
Q: What's the difference between doxxing and swatting? A: Doxxing is the exposure of personal information; swatting is making false emergency reports to send armed police to someone's address. Swatting often relies on doxxed address information but represents a distinct and more immediately dangerous escalation.
References and Further Reading
This comprehensive guide draws on extensive research from government agencies, academic institutions, cybersecurity firms, and privacy advocacy organizations. Below are the primary authoritative sources that informed this analysis:
Doxxing Statistics in 2024
SafeHome.org (2025)
Comprehensive statistical research on doxxing prevalence in the United States
BlackCloak Identifies Surge in Doxxing and Swatting Threats on Corporate Executives
BlackCloak (Cybersecurity Firm) (2023)
Industry report on executive-level doxxing threats and protection strategies
Protecting Law Enforcement from Doxxing: Balancing Officer Safety and Constitutional Oversight
Police1.com (Law Enforcement Publication) (2025)
Legal analysis of anti-doxxing legislation and constitutional considerations
Doxing Victimization and Emotional Problems among Secondary School Students
National Institutes of Health (NIH/PMC) (2018)
Peer-reviewed research on psychological impacts of doxxing victimization
What is OSINT (Open Source Intelligence)?
SentinelOne (2025)
Technical explanation of OSINT methodologies used in doxxing attacks
Data Broker Database
Privacy Rights Clearinghouse (2025)
Comprehensive database of data brokers and consumer privacy resources
Remove My Private Info from Google Search
Google Support (2025)
Official Google documentation on removing personal information from search results
What is Two-Factor Authentication (2FA)?
Fortinet (2024)
Authoritative guide on 2FA security implementation for doxxing prevention
Is Doxxing Illegal? Doxxing, Free Speech, and the First Amendment
Foundation for Individual Rights and Expression (FIRE) (2023)
Legal analysis of doxxing and First Amendment considerations
The Best Data Removal Services of 2025
The New York Times Wirecutter (2025)
Independent review of professional data removal and privacy protection services
About DisappearMe.AI
DisappearMe.AI provides comprehensive privacy protection services for high-net-worth individuals, executives, and privacy-conscious professionals facing doxxing threats. Our proprietary AI-powered technology permanently removes personal information from 700+ databases, people search sites, and public records while providing continuous monitoring against re-exposure. With emergency doxxing response available 24/7, we deliver the sophisticated defense infrastructure that modern privacy protection demands.
Protect your digital identity. Contact DisappearMe.AI today.
Related Articles
Doxxing Defense 101: Protecting Your Family in a Remote-First World
Comprehensive doxxing protection guide for families in remote work environment. Learn how to prevent personal information exposure, protect children from online harassment, and secure family's physical address from workplace disclosure.
Read more →Why Did I Get Doxxed? 14 Expert Answers to Protect Executives, High-Net-Worth Individuals & Public Figures in 2025
Discover why you were doxxed, how attackers found your personal data, and 14 expert strategies to remove exposure, protect families, and prevent future attacks.
Read more →13 Critical Doxxing Questions Answered: Advanced Protection Strategies for 2025
Expert answers to the most difficult doxxing questions executives and privacy-conscious individuals ask. Comprehensive strategies beyond basic protection.
Read more →What to Do Immediately After Being Doxxed: Hour-by-Hour Emergency Plan (2025)
Doxxed? Follow this hour-by-hour emergency plan. Immediate actions to protect yourself, remove exposed info, and recover your privacy. Call 424-235-3271 for help.
Read more →